Diffie Hellman Key Exchange
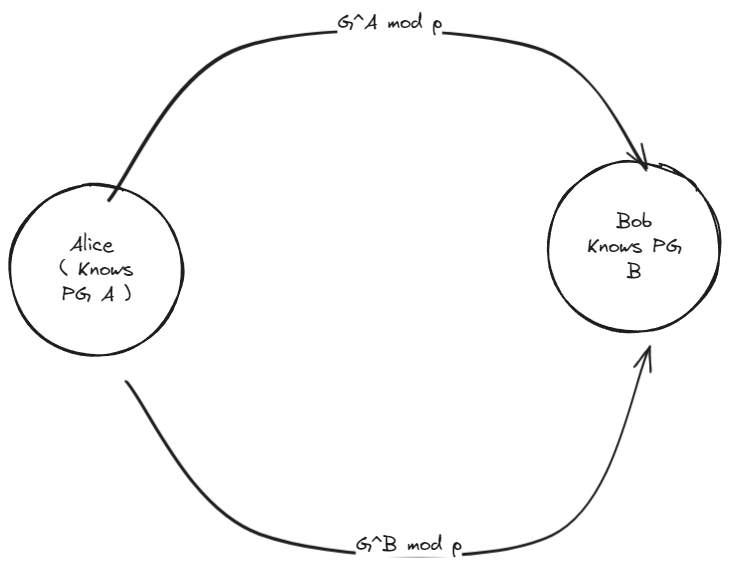
Alice and Bob agree on a prime number and a base .
- Alice chooses a secret number and sends Bob
- Bob chooses a secret number and sends Alice
- Alice computes
- Bob computes
Example
Alice and Bob agree on:
Alice chooses .
Alice’s Calculation:
- Alice computes her public key:
- Alice sends to Bob.
Bob’s Calculation:
- Bob chooses a secret number .
- Bob computes his public key:
- Bob sends to Alice.
Shared Secret Calculation:
-
Alice computes the shared secret using Bob’s public key:
-
Bob computes the shared secret using Alice’s public key:
Thus, both Alice and Bob now share the same secret key .
Diffie-Hellman with and
-
Alice and Bob agree on:
-
Alice’s Secret Number:
- Alice chooses .
-
Alice’s Public Key:
Compute .
-
Bob’s Secret Number:
- Bob chooses (e.g., ).
-
Bob’s Public Key:
Compute .
-
Shared Secret Computation:
- Alice computes .
- Bob computes .
Now, both Alice and Bob have a shared secret key they can use for encrypted communication.
RSA Encryption
the RSA (Rivest, Shamir, and Adleman) algorithm, which is a widely used asymmetric cryptographic algorithm. The content covers the key aspects of RSA, including the generation of keys.
Key Points from the Slide:
-
RSA Basics:
- RSA involves a public key and a private key.
- The public key is broadcasted and used for encrypting messages.
-
Key Generation Steps:
- Choose two distinct prime numbers and .
- Compute , where:
- is used as the modulus for both the public and private keys.
- Compute Euler’s Totient Function, .
-
Algorithm Processes:
- Key Generation
- Encryption
- Decryption